5.7.5 Permanent Error Evaluating DMARC FIXED
8 min read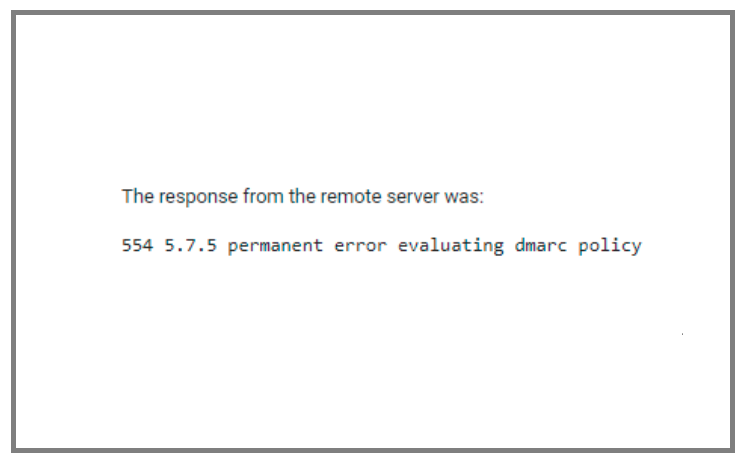
Have you been getting the “5.7.5 permanent error evaluating DMARC policy” while sending emails from your domain? The “5.7.5 permanent error evaluating DMARC policy” is a common error that stops the SMTP ports from accepting emails from your domain. The issue usually happens due to a combination of settings in the SPF record, DMARC record, or email service.
In this guide, we’ll describe how to resolve this issue quickly and easily.
Reasons behind 554 5.7.5 Permanent Error Evaluating DMARC Policy
If you are facing a “5.7.5 permanent error evaluating DMARC policy”, here are some common reasons behind this error:
Incomplete DMARC Settings
When you set up DMARC, you can either choose to use p=none or p=quarantine/reject. If you use the p=none policy, then make sure that your SPF and DKIM pass on the message. Otherwise, it will fail the DMARC policy evaluation.
Incorrect DKIM email authentication record
DKIM stands for DomainKeys Identified Mail. It is a method of verifying the authenticity of the email sender, which prevents malicious actors from impersonating the email sender’s domain name.
Sometimes you might face issues with your DKIM authentication. A mismatch between the “d=” tag in the DKIM signature, and the sending domain, will result in a failed DMARC evaluation.
For instance, if you have changed your domain name and have not updated it in DKIM records, then it will fail the DMARC policy evaluation as well.
Incorrect SPF Record
SPF stands for Sender Policy Framework. It is an email authentication technique used to verify whether an email message comes from a valid sender’s server or not.
DMARC works by checking SPF records to verify if they are valid or not. You must ensure that the SPF records are configured correctly and work with your domain name to avoid this error.
Wrong Policy Evaluation on Recipient Side
If the receiving server is incorrectly evaluating your DMARC policy settings then that may lead to this error as well. That means that the recipient server is rejecting emails because of its own policies, not because of anything wrong with your DMARC settings.
To avoid this issue, make sure that all of the above-mentioned points are properly configured in order to pass policy evaluation on the recipient side.
Afterward, talk to the recipient and ask them to evaluate their own DMARC.
How to Fix 554 5.7.5 Permanent Error Evaluating DMARC Policy
1) Remove Extra Characters From The Record
The error 5.7.5 permanent error evaluating DMARC policy can be caused by a different number of reasons, however, the most common ones are:
- incorrect quotation marks
- extra characters or symbols in the record
- a missing semicolon at the end of the record
Here’s an example of a record that gave this error:
| v=DMARC1; p=none; rua=mailto:Demarc@onmicrosoft.com; ruf=mailto:Demarc_forensic@onmicrosoft.com; fo=1:d:s. |
This record might look fine to you at first, but on testing it, we got the “5.7.5 permanent error evaluating DMARC policy” message.
When we checked again, we realized that there was an extra dot at the end of the record—if you look closely at the same record above, you can see that there is a period (dot) (.) at the end.
Once we removed that dot and ran the test again, it worked perfectly.
Here’s how the same record looked with no errors:
| v=DMARC1; p=none; rua=mailto:Demarc@onmicrosoft.com; ruf=mailto:Demarc_forensic@onmicrosoft.com; fo=1:d:s |
2) Change Your SPF Record From Neutral
If you’re getting an error message that says “5.7.5 permanent error evaluating DMARC policy” when you’re trying to send an email, it’s probably because your SPF record is set to Neutral.
SPF stands for Sender Policy Framework, and it helps make sure that the mail server from which an email is sent is legit. It’s not good enough just to have a server that sends emails; there needs to be some verification that the server is legit. That’s what SPF does: it verifies that your mail server has the right credentials.
Why can’t your SPF record be neutral?
Because if messages are allowed to be sent through a neutral server, scammers could send fake emails using your domain name, which means people might think they’re real when they aren’t—and end up clicking on links or downloading files they shouldn’t.
That’s why you should at least change your SPF record to softfail ~all or hardfail -all when you implement DMARC—so that people know a message from your domain name is probably safe.
3) Check If Your Email Service Provider Supports SPF Aligned Emails
One of the most common reasons for receiving this error is that your email service provider doesn’t support SPF-aligned emails.
Email providers like MailChimp and ProtonMail have their own SPF records, and when you send emails through them, they’re not sending SFP-aligned emails. As such, it’s important for you to check your email service provider’s SPF disposition type to see if it supports SPF-aligned emails.
If it does, then your DKIM signature will be modified during the sending process so that the From address aligns with your own domain (instead of with MailChimp’s domain) and ensure that you pass the DMARC policy evaluation.
If it does not, then you’ll need to use a different email service provider (or change your existing provider’s settings) so that you can send SPF-aligned emails.
4) Change p=none Policy For DMARC
If you’re getting a “5.7.5 permanent error evaluating DMARC policy” error, it means that the DMARC policy on your domain is preventing you from sending your emails. To fix this, you just need to change your DMARC record with your DNS provider to have a p=none policy.
The DMARC policy tells email providers what to do with emails that fail the SPF and DKIM checks: reject them or quarantine them. If you want to send emails even if those checks don’t pass, you can relax your policy temporarily by setting it to p=none in your DNS settings.
This is called a “relaxed policy”, so it’s not recommended for email spoofing prevention. But changing your DMARC policy to p=none will allow you to temporarily send emails without getting DMARC errors.
For example, you could change this record:
| _dmarc.yourdomain.com TXT “v=DMARC1; p=reject; fo=1 |
to this:
| _dmarc.yourdomain.com TXT “v=DMARC1; p=none; fo=1 |
What does this mean for you? You can send your email even if it doesn’t pass DMARC. However, you’ll want to revert back to a p=reject or p=quarantine policy in order to prevent email spoofing on your domain.
5) Set Up DomainKeys Identified Mail (DKIM) Authentication
If you’re getting the error message “5.7.5 permanent error evaluating DMARC policy”, it means that you haven’t enabled DomainKeys Identified Mail (DKIM) email authentication on your domain—and in order to pass DMARC, you have to have a DKIM email authentication record set up.
To do that, here’s what you need to do:
- Select the “I will manage my email authentication” option on the Settings page of your account.
- Enter the domain name in the DKIM field and click Save.
- Copy the generated TXT record name and TXT record value into your web host DNS records
DMARC Policy Formatting Requirements
DMARC is an email authentication protocol that allows recipients to verify that emails purporting to be from your domain are actually coming from your domain. This guide will outline some of the important formatting requirements when setting up DMARC for the first time.
➤ First, your DMARC record must begin with “v=DMARC1”. This lets email providers know that the record is formatted according to the version of DMARC that’s currently being used (which is 1).
➤ Next, specify your policy. The policy must be either p=none or p=quarantine or p=reject. This tells email providers what to do when an email fails authentication checks.
➤ The policy should be the second value in the record. The policy can be one of three things: p=none, p=quarantine, or p=reject. “None” means that you want the email provider to do nothing when it sees a suspicious email from your domain—it will simply leave it alone, and might even deliver it. “Quarantine” means that you want suspicious emails from your domain to be delivered as spam or junk mail instead of being delivered as normal mail. Finally, “reject” means that you want suspicious emails from your domain to be rejected and never delivered at all.
➤ Use colons as separators between values — it’s a good idea to use colons and not semicolons. Semicolons can cause problems, especially when multiple values are specified on a single line.
➤ Don’t use extra characters or bad quotes. Excess whitespace at the end of lines will be treated as part of the record, which can cause problems.
Here’s an example of a good DMARC record:
| v=DMARC1; pct=100; p=reject; rua=mailto:dmarc@example.net; mailto:dmarc-rua@example.com; aspf=s |
How To Find Errors In DMARC Record Policy
Having a DMARC record is a good step toward securing your email communication. However, if there are any errors in it, the entire system will be ineffective. This is why it’s important to find any errors and resolve them as soon as possible.
The best way to do this is by using the DMARC lookup tool by PowerDMARC. The tool checks whether or not your record is valid and shows you any potential errors. You can use the tool for free by following these steps:
- Visit DMARC Lookup Tool by PowerDMARC.
- Enter your domain name into the empty field.
- Once your record has been checked, the tool will show you an overview of the entire database.
- If there are any errors, they will be highlighted on the page.
- Once you know where the errors are coming from, you can resolve them easily using the instructions provided with each error message.
Are You Worried About The Security Of Your Business Emails?
It’s a real concern. In fact, many cyber attacks start with an email. But that doesn’t mean you have to give up on reaching your customers through email!
Instead, secure all your business emails with email authentication services by PowerDMARC. This will help you gain the trust of your customers and protect your brand from phishing attempts by hackers and other bad actors.
With PowerDMARC, you can ensure that any emails coming from your company are not only safe for customers to open, but also easy for them to identify as legitimate communications from your brand by placing your business’s seal on them.
We know that protecting the integrity of your company name and image is important to you, and we want you to be able to do it in a way that makes sense for both parties involved—so that’s why we offer this service at an affordable price point while still giving our clients access to all of our expertise on email authentication techniques.




